Distributor Watermarking : Insure against pre and post release piracy threat landscape
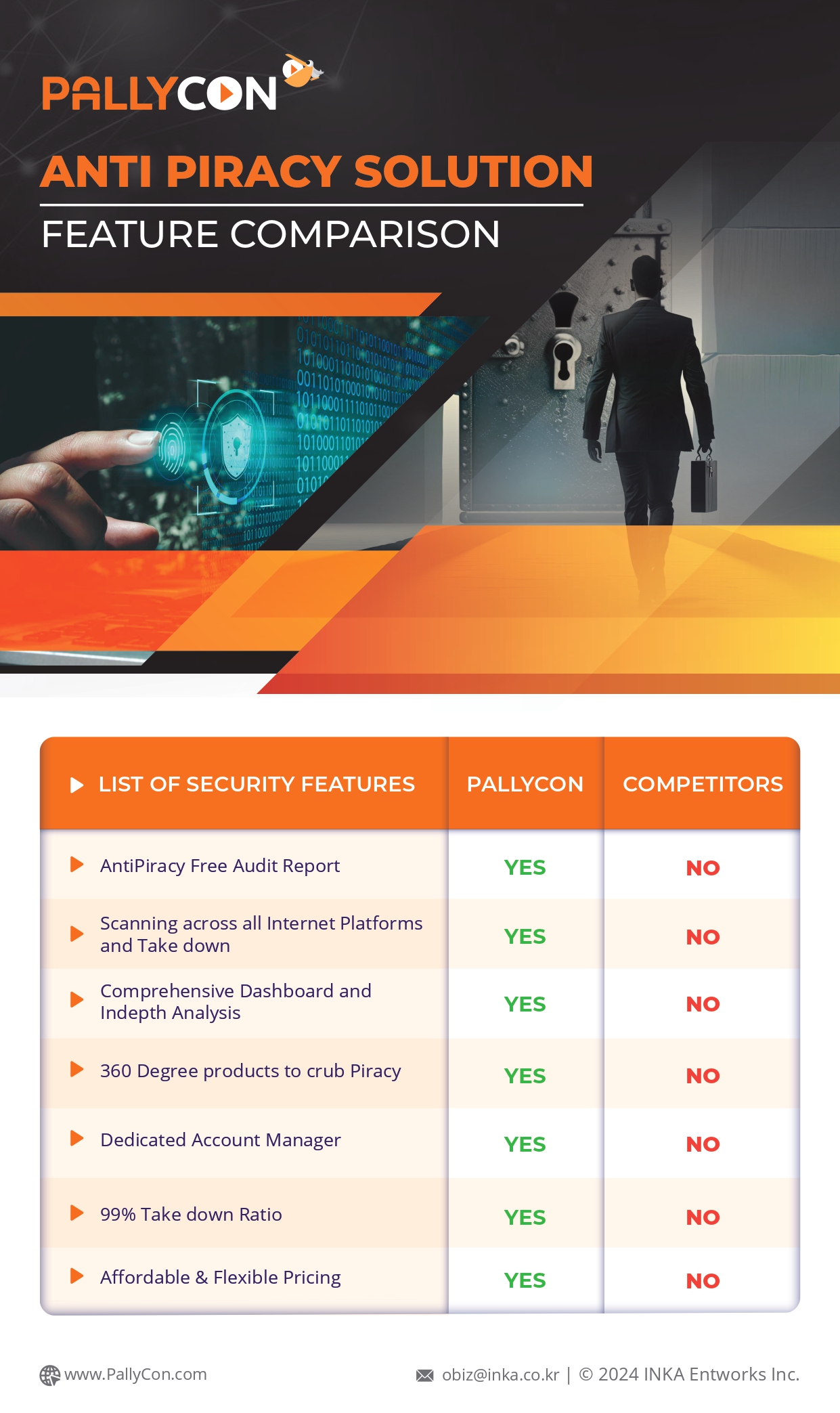
Streaming has taken over as the most popular method of content consumption today. The volume and scope of content piracy has grown as a result. In order to identify the source of infringement and limit access to premium content, studios, OTT providers, and content owners now absolutely require anti-piracy and content protection technologies. While DRM protection can be used by content owners to stop unlawful access to their material, forensic watermarking solutions are required to pinpoint the precise location of pirated broadcasts without degrading the viewer experience. In contrast to forensic watermarking, which is often tracked at each user who is consuming the content, distributor watermarking enables the content distribution end to trace each copy of the content being syndicated to the platforms. Distributor watermarking is used for the following reasons:
- To prevent piracy: Watermarking can help deter piracy by making it easier to trace the source of unauthorized copies of the content.
- To track usage: Watermarking can be used to track the use of the content, including how it is being shared and where it is being viewed. This can be useful for understanding the distribution and reach of the content, as well as for identifying any unauthorized use.
- To protect against tampering: Watermarking can help detect and prevent tampering with the content, such as by altering or deleting parts of it.
- To enforce licensing terms: Distributors can use watermarking to enforce licensing terms and ensure that the content is only used in accordance with the terms of the license.
- To prove content ownership: Distributors can use watermarking to prove their ownership easily.
PallyCon Distributor Watermarking
PallyCon Distributor Watermarking (DWM) is a watermarking solution that is imperceptible, robust to attacks and helps track illegally leaked video content. It can detect the watermark information from both the leaked video and a single video frame captured using any device, such as a smartphone camera. It inserts the channel information into the original video in the form of an invisible watermark. Additionally, it offers the choice of adding visible watermarks.
The CLI (Command Line Interface) tool used for the watermark embedding in PallyCon DWM comes in the following two versions:
- DWM PreEmbedder: Used to insert the distribution channel’s watermark into files in the Mezzanine or MP4 formats
- DWM DRM Embedder: Used when the dual protection of Multi-DRM + forensic watermark information needs to be added to MP4 video files streaming DASH/HLS format
Related Article – PallyCon Distributor Watermarking Guide
The PreEmbedder will then create a separate version of the video for each channel, with a unique watermark added to each one. Finally, the corresponding DWM video should be delivered to each distribution channel, which may involve uploading the video to the channel’s website or platform, or providing a link for the video to be downloaded from a secure location.
In the event of a content leak, it is possible to use PallyCon’s detection service to identify the source of the leak. To do this, the leaked content should first be posted on a downloadable link and registered on the PallyCon Console. PallyCon’s service will then extract any watermark present in the leaked copy and use it to deliver the channel information (also known as the Distributor ID) to the customer. This information can be used to help identify the source of the leak and take appropriate action.
PallyCon DWM PreEmbedder is a DWM embedding utility for Linux that uses the CLI (Command Line Interface) which can be hosted on remote VM such as GCP, AWS , etc simple tutorial of applying Distributor watermarking video is available at https://www.youtube.com/watch?v=WO2YCYzRJPE&t=144s
Supported Specifications :
| Item | Specification | Remarks |
| Content Type | Supports video contents only | |
| Format and codec | MP4(H.264, H.265, XDCAM), MOV(ProRes), MXF(XDCAM) | DWM DRM Embedder supports MP4 format only while DWM PreEmbedder supports formats as mentioned |
| Supported Resolution | Up to 4K/UHD resolution | |
| Dynamic Range | SDR (Standard Dynamic Range), HDR (High Dynamic Range) supported | |
| Number of DWM ID | Up to 4095 unique IDs of recipients per PallyCon DWM account | |
| Minimum Video Length | Need at least 30 seconds of recorded video to detect watermark | The quality of video should be good and it should be blur or shaky |
| Video Quality for Detection | Need 480p 1Mbps or higher video quality for detection. | 720p video is recommended. |
| Number of recipients | Max 4096 recipients per site ID of DWM account | |
| Single Frame Detection | Even if only single frame is captured of watermarked content then in certain cases it can reveal the source of the video distribution |
To run the DWM PreEmbedder, you will need a system with certain hardware and software requirements. In terms of hardware, you will need an Intel CPU and at least 8GB of RAM, as well as an NVIDIA graphics card that supports hardware-accelerated video encoding and decoding. In terms of software, you will need to have a supported operating system such as Ubuntu Server 18.04 or 20.04, or CentOS 7. Additionally, you will need to have the Intel IPP (Integrated Performance Primitives) 2018 software installed, as well as the NVIDIA CUDA Toolkit 9.1 or later for hardware acceleration. Finally, you will need to have any necessary dependency libraries installed.
Related Article – How does Watermark Embedder use Cloud Servers to Mix A-B Segments of Protected Videos?
Thus, forensic video watermarking technology helps identify safe routes, allowing studios to penalize unreliable distributors while rewarding those with strong security. With the incorporation of an encoder, this can enable both secure live content and VoD as a cloud service. Video broadcasts can potentially contain undetectable watermarks that are particular to each subscriber. Therefore, content owners can identify the exact account that was the source of the leak and suspend it in the event that the asset is distributed illegally. In order to find the offending user or channel, the video can also be tracked back to the last approved recipient.

PallyCon provides cloud-based SaaS multi-DRM solution and Forensic Watermarking service. Cloud services built on AWS enables you to use services in the cloud. Get started contents protection quickly and easily with PallyCon.