Analysis of Live Stream Piracy in OTT
Understand how pirates attack live sporting events and ways to stop piracy across platforms
Live sports and events are at the heart of the broadcast industry, for which dominant companies pay a huge sum in broadcasting rights. However, the popularity of live streaming content makes it a prime target for piracy. Every year, billions of dollars are spent on the media rights of premium live content. This has also led to pay TV services becoming more expensive, as they compete for viewers and subscribers.
With the increasing ease of access to content, the challenge of protecting it from pirates has become more complex than ever before. According to a piracy data company, people have made 362.7 million visits to sports piracy websites in January 2019 alone. This leads to huge losses in revenue for the entire commercial chain, from the media rights owners to broadcasters, including both traditional and OTT delivery platforms. With increasing internet penetration and speed, streaming piracy has become even more accessible to wider audiences, and the quality of the pirated streams has also improved substantially. HD 720p is currently the most popular resolution for live sports streaming piracy, since it delivers good quality content on large screens with minimal buffering.
Three Sources of OTT Live Stream Piracy
 |
 |
 |
|
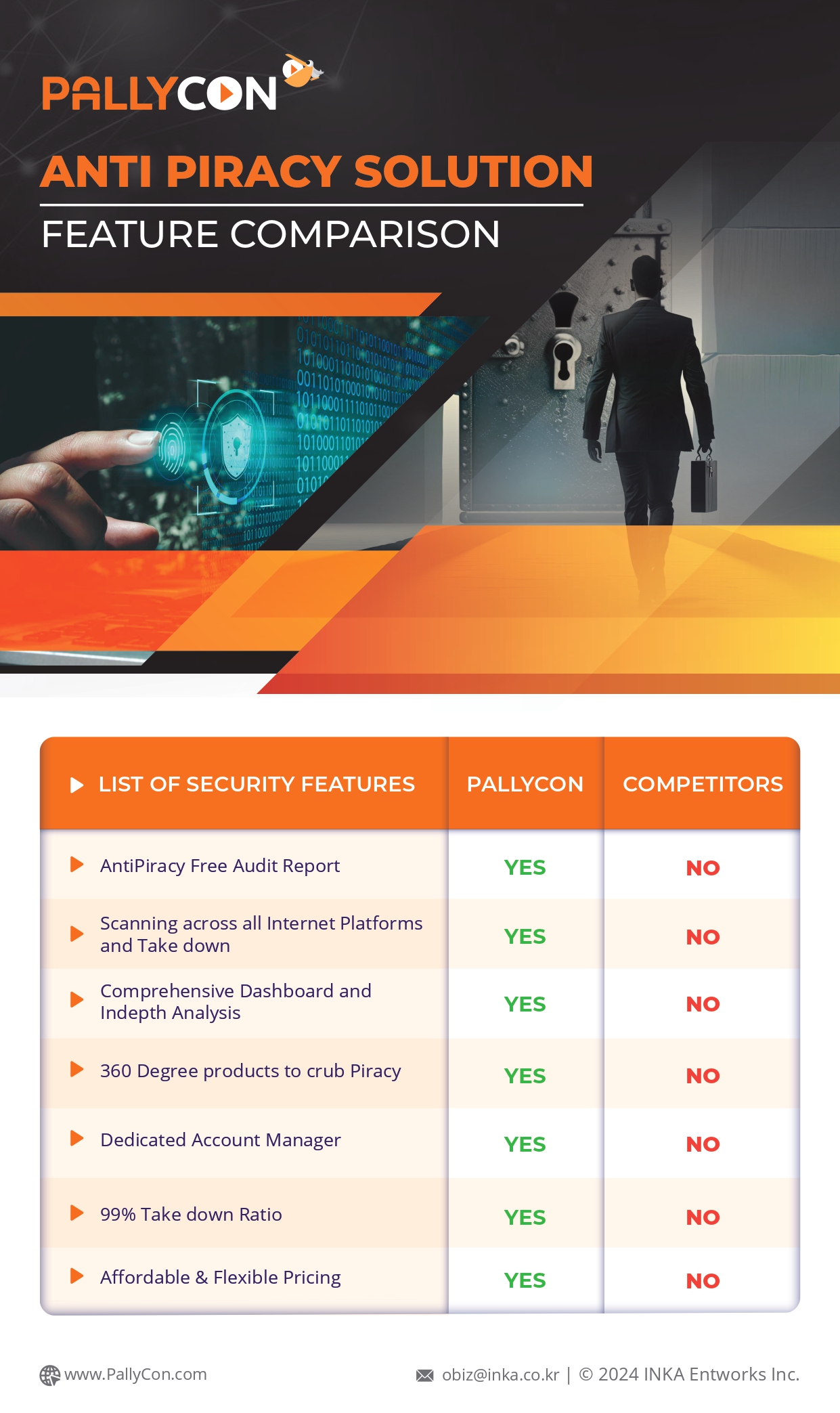
| Source | External Camera | Screen Recording | HDCP Stripper |
|---|---|---|---|
| How to ‘re-stream’ | Screen → Camera → Streaming device → Streaming server and CDN (for scalability) | PC with broadcast s/w (e.g. OBS Studio) → Streaming server / CDN | PC or OTT device → HDCP stripper → Streaming device → Streaming server / CDN |
| Quality | Low | High | Very high |
| Popularity | Low | Very high | High |
| Major attacks to forensic watermarking | D2A conversion, Resizing, Frame rate change, etc | Resizing, Frame rate change, etc | Resizing, Frame rate change, Collusion attack |
Illegal Acquisition of Live Content
CCcam card-sharing
The sources of streaming unauthorized live content are several and vary from case to case. However, a majority of them are from satellite content. The most predominant method of content acquisition from satellites is CCcam card-sharing (also called control word sharing), which can affect all satellite providers that use DVB-CSA scrambling. It allows multiple client devices to access subscription services based on an aggregation of authorizations of valid subscription smart cards. The decrypted control word being sent from the smart card to the host box is then captured by a network intercept, which forwards the decrypted control word (64 bit) from one card to a CCcam server. All devices which are connected to this server can then access the conditional access keys stored on it and view all the content that the first smart card was authorized to receive. DreamBox is one of the major receivers in this category, while other Linux-based satellite receivers, such as Enigma, Enigma2, etc., can also be modified to use the CCcam server system.
Related Article – Securing OTT Content with Multi-DRM & Forensic Watermarking
Basic Interoperable Scrambling System-Encrypted (BISS-E)
Another method by which satellite content can be pirated is by publishing the satellite locations and their associated BISS keys. The Basic Interoperable Scrambling System-Encrypted (BISS-E) key can decrypt all the entitlement control messages (ECMs) for a satellite when entered into a decoder. Along with BISS keys, hacking websites also post discovered satellite keys for other systems, such as Viaccess, Viaccess 2, Conax, Cryptoworks, NDS Videoguard, Mediaguard (seca), and Nagravision 1 & 2. While cable video operators employ video delivery technologies to prevent bulk acquisition, authorized users can still share their content if proper security measures are not implemented. Authorized content can be redistributed in various ways starting from a single stream via social media to HDMI streamers capable of taking up 24 HDMI ports and converting them to IP streams. CableCARD-enabled devices, such as infiniTV6 PCIe, Hauppauge WinTV-quadHD, SiliconDust HDHomeRun, etc., offer varying levels of capture/streaming capability which help in wide scale leakage of content. IPTV providers also offer hundreds of free-to-air (FTA) channels which can be acquired en masse and redistributed. Devices that can split HDMI and remove HDCP content are also readily available for very low costs. In addition, the easy access to commercial grade HDMI streamers which can take from eight to twenty-four input ports while creating an output stream has led to increase in “home-brew” streaming of popular live streaming events, such as Olympics and World Cup matches. These devices also allow the users to compare two input sources in order to detect and remove the hash codes used in watermarking.
Live content on OTT platforms can also be captured using off-the-shelf screen recording, HDMI-capture devices, streaming software and HDCP strippers.
Illegal Distribution of Live Streams
In satellite acquisition, a protocol called SAT>IP allows satellite-delivered DVB-S/S2 RF signals to be demodulated and converted to IP right at the point of reception in a SAT>IP server. This further accelerates the ease of acquiring encrypted video content. Several open source products, such as TVHeadend, are also available which can run on multiple platforms (Linux, FreeBSD, Android, and Raspberry Pi). These devices can take in video from almost any source, such as DVB-S/DVB-S2 (satellite), DVB-C (cable), DVB-T (terrestrial), ATSC (over the air), IPTV (any IP source), SAT>IP, local or network reachable file libraries and HDHomeRun, to output multiplexes, assign EPGs to streams, and schedule recordings.
PC video players and Kodi add-ons can receive and play TV streams from the TVHeadend server. However, the only limitation to programs like TVHeadend is that the number of connections that can be made to the server is limited. Hence, many IPTV providers “restream” from different sources. TVHeadend outputs a playlist in the M3U format, which can be consumed by almost any media player and be used in Infomir-based devices as well as on Kodi add-ons directly. Re-streamers subscribe to different IPTV services and combine the content of multiple playlists to output a single playlist which is, then, freely published.
Related Article – Multi-DRM – An Antidote to Video Piracy Landscape
Countermeasures for Illegal Live Streams
Software updates
Card sharing is of major concern to live broadcasters and pay-TV companies. Hence, some countermeasures have been undertaken to permanently prevent it. One technical method is to update the software of digital receivers provided by the subscription television service which implements a further decryption layer held within the receiver. Thus, instead of sending a plain text control word from the smart card to the receiver’s microprocessor, which can be intercepted, the decrypted ECM can act as an encrypted control word, which can be decrypted only by a legitimate receiver.
Control-word changes
Another simple method to bypass card sharing is to increase the frequency of control-word changes, which puts extra stress onto the card-sharing system. In addition, the card can also be linked with the connected device (set-top box, CAM module, etc.), so that it can only be used on that particular device. The standard specification can also be updated to the DVB-CSA3 system, which has an AES-based 128-bit key system for better encryption. It is hardware friendly and software unfriendly, thereby preventing reverse engineering of the system, which is required for card sharing.
OTT controls
Piracy on streaming and OTT platforms can be detected using video fingerprinting techniques. For rapid fingerprinting, since time is of essence in the case of live content, the video fingerprint should be lightweight in terms of data size. Additionally, it should withstand the piracy attacks and work across all key video formats, including 4K, HD, and SD as well as both traditional and OTT delivery. Once illegal content is identified using fingerprinting, the entire network path can be evaluated to determine the host within seconds. The source of the streaming piracy can then be determined by analyzing the subscriber-level forensic watermarking. Efficient video watermarking solutions must be robust against piracy attacks, such as collusion and resizing attempts. They should also operate across devices including legacy devices.
Hence, while premium live sports is under great threat from increasing piracy worldwide, content distributors, pay-TV operators, and broadcasters can deploy end-to-end security systems based on DRM protection, advanced monitoring, and forensic watermarking. These measures can help reduce premium live streaming piracy and save critical revenues for the OTT and broadcasting industry.

PallyCon provides cloud-based SaaS multi-DRM solution and Forensic Watermarking service. Cloud services built on AWS enables you to use services in the cloud. Get started contents protection quickly and easily with PallyCon.