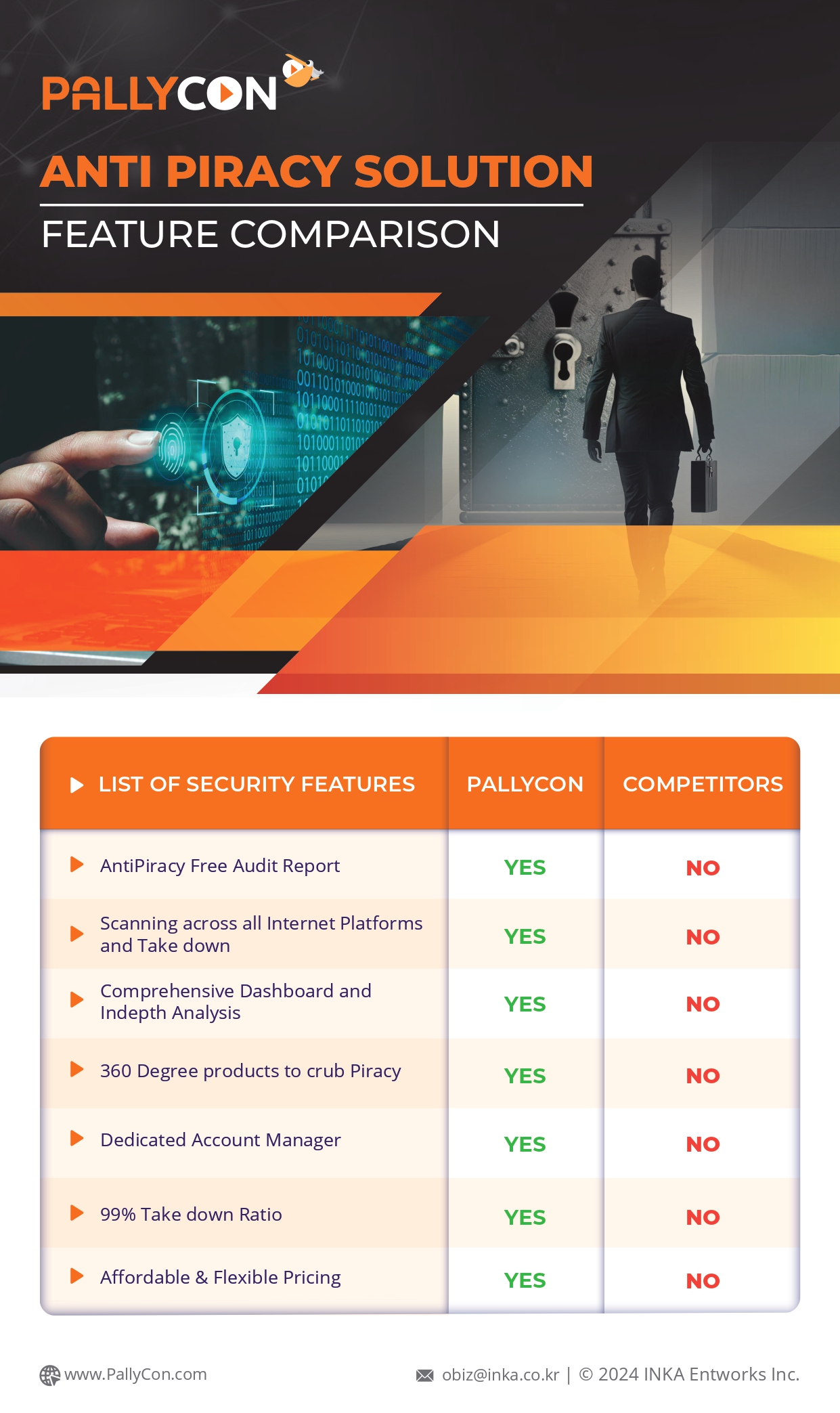
Forensic Watermarking – The Armor Shield in your Fight Against Content Piracy
Why use Forensic Watermarking?
Piracy has come to threaten the premium content market in more ways than one. The illegal capture, recording, and distribution of premium content impacts the end-to-end content workflow – creators, owners, and distributors. It has become commonplace to retrieve the pirated copy of your favorite Avengers movie right on the day of the release!
Though this may seem harmless to the end user, the creators, owners, and distributors of the premium content incur notable business losses. In 2022, pirated video material got over 230 billion views, costing the US economy a whopping $229 billion, including TV, movies, and sports piracy.
Worse, the situation can deteriorate if companies do not start adapting their content security strategies with the right mix of security solutions. The piracy threat landscape looks grim, and the only sustainable armor for content owners and distributors to protect their revenue stream and ensure growth with agility is to make Forensic Watermarking the fulcrum of their security suite.
Forensic Watermarking – A short primer
Forensic Watermarking (FWM) complements other content protection technologies like Digital Rights Management (DRM) by protecting content through identification. The technology involves inserting an imperceptible digital watermark in every legible video copy meant for the recipients.
This watermark consists of unique identifiers with metadata. This mechanism tracks an end-to-end trail from video content source through its various distribution points and recipient points.
Forensic Watermarking, in essence, protects the rights and interests of content creators against the illegal distribution of copyright content and also helps in providing authenticity of content ownership.
Who can benefit from using Forensic Watermarking?
We saw above what goes behind the workings of FWM. Let us now shift our focus towards two primary use cases for FWM implementation – Hollywood Studios releasing premium 4K/UHD quality video content and Live Streaming and broadcasting operators.
For studios producing premium UHD/4K video/ VOD content, FWM is a critical element to help discover vulnerabilities in the entire distribution workflow.
FWM has become an indisputable piece of evidence for Live Streaming broadcasters to detect any illegal source of piracy or redistribution, help disrupt in real time issue & takedown notices, to curb piracy thereby saving revenue.
Related Article – Forensic Watermarking for Premium Online Video Contents
Different types of Forensic Watermarking
FWM can be used both as a preventive and a reactive anti-piracy mechanism. It helps in detection and helps take down any illegal pirated copies. The technology empowers content owners and distributors to detect camcording and applies cloud-based session-based watermarking, robust against Digital-to-Analog conversion.
FWM implementations should maintain a balance between the watermark robustness against a range of piracy threats (like recompression and screencasting) while remaining undetectable and not interfering with the viewing experiences of the end-user.
There are primarily two ways of applying FWM:
- Client-side watermarking requires watermark embedding within the end-user’s devices and is vulnerable to hacks such as removal of watermark & significant high cost to support a myriad of streaming devices, makes it less favorable to adoption by streaming vendors
- Server-side watermarking includes real-time dynamic watermark insertion with end-user ID, independent of end-device or need to integrate with client player solution and scalability makes it a go to solution in the streaming world. This mechanism establishes the traceability of any content independent of the device with additional information of device location using IP address etc. also easy to cause disruption during the streaming process.
Behind the workings of PallyCon’s Forensic Watermarking solution
PallyCon Watermarking is a cloud-based SaaS that allows easy application of watermarking without building complex server environments.
There are broadly three steps to apply PallyCon FWM on your premium content, flexible enough based on requirements.
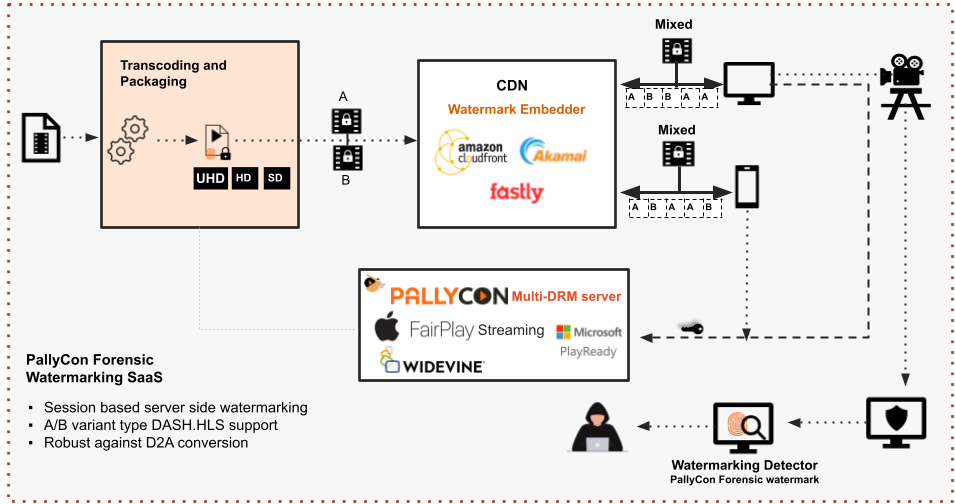
The above diagram depicts the end-to-end FWM workflow.
Step 1: Transcoding and Packaging
FWM workflow starts with Transcoding and Packaging the source video file, where you need to sign up for an account on PallyCon Console for transcoding, watermark pre-processing, and content packaging on the cloud.
You need to set the AWS region to run the packaging service on source video and different storages for packaging input and output, along with information on S3 storage configuration like bucket name, access key, and secret key. Upload the source video to Amazon S3 storage and create a Transcoding and Packaging job on the PallyCon console.
The PallyCon SaaS creates A/B variants of the video, packages them into DASH/HLS streams, if required content can be encrypted with Multi-DRM and stores the result in the output storage as registered.
PallyCon’s Transcoding and Packaging service is a complete end-to-end SaaS-based solution to transcode and apply multi-DRM encryption and forensic watermarking in a single workflow.
There are two options to use PallyCon’s Transcoding and Packaging service.
Option 1: Transcoding and Packaging using the PallyCon console (UI based)
Option 2: Transcoding and Packaging using the REST API, which can be easily integrated in existing streaming workflow.
Related Article – Transcoding & Packaging Service Guide
Step 2: Session Manager
Once the A/B variant contents are generated and kept ready for streaming, the next step is the playback URL generation consisting of the unique watermark sequencing information required for content mixing at the edge server in real time. The process of generating the unique playback URL is handled by PallyCon’s Session Manager via REST API. The information that needs to be passed for unique URL generation are: domain of content URL, output path of content, content ID, streaming protocol (DASH/HLS), forensic mark (special info such as device id, Ip address, location etc), watermark type JWT or AES.
When a Playback request is made by the viewer, the streaming service provider requests PallyCon’s Session Manager to provide a unique playback URL. This URL is used in the next step called watermark Embedding.
Step 3: Watermark Embedding
CDN edge does the A/B variant type watermark embedding either as pre-integration or with an embedder module.
The player on the client device using the unique playback URL makes a request to CDN to start the streaming. The CDN edge server picks and delivers the unique A/B video segments as per the requested URL i.e. A/B variant stream is mixed based on the watermarking pattern in URL, and the client player plays the watermark-embedded stream as is.
In the case of Amazon CloudFront, the content URL and session data are sent to the PallyCon session manager. The unique Session URL is generated from the stream URL and session key, which is sent to the client player to start playback. The watermark-embedded stream is played similarly to the non-watermarked stream.
Related Article – Forensic Watermarking Integration Workflow
Watermark Detection
If the watermarked video generated as a result of the above steps gets leaked and becomes illegally available for distribution through streaming sites, you can request watermark detection by sending the video via the PallyCon console or API.
Watermark detection is a forensic analysis process where from each video frame the original unique AB watermark pattern is extracted and decrypted using the secret key. This analysis reveals the viewer responsible for illegal distribution. For this process, a continuously recorded video of at least 5 minutes, with a minimum of 480p with 1 Mbps, is required.
Conclusion
As the digital landscape and consumer consumption preferences are evolving, so are the piracy threats. PallyCon’s robust Forensic Watermarking has completed globally acclaimed Cartesian’s Farncombe Security AuditTM Watermark against various piracy attacks such as reencoding, cropping, filtering, and camcording. Start your content security journey with PallyCon with a free trial today and shield your premium content!

PallyCon provides cloud-based SaaS multi-DRM solution and Forensic Watermarking service. Cloud services built on AWS enables you to use services in the cloud. Get started contents protection quickly and easily with PallyCon.