Forensic Watermarking for Premium Online Video Contents
With the growing popularity of video streaming, OTT platforms, studios, and pay-TV operators are making huge investments to create high-quality content. But potential losses due to piracy remain an ever-present threat.
The platforms and studios now want content creators to use advanced security measures for content protection. This is to ensure that the video content remains protected throughout its lifecycle, right from production, promotion, distribution, to consumption.
While DRM (Digital Rights Management) is getting increasingly popular among creators and digital platforms, it can be combined with forensic watermarking for advanced content protection.
When blended together, DRM and video watermarking function as a powerful deterrent to the cybercriminals as it enables the platforms to prevent misuse of their content and even identify the source from where the video content was leaked.
What is Forensic Watermarking?
Forensic watermarking, also known as digital watermarking, is the process of embedding imperceptible sequence of code or information directly into the video content. The code is embedded at random locations within the content, which can only be detected by a watermark detector software.
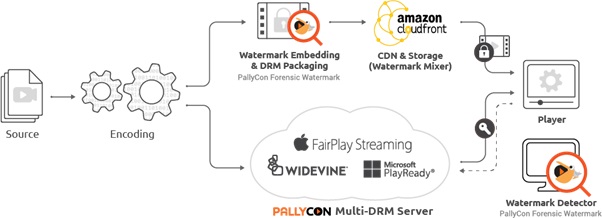
PallyCon Forensic Watermarking with Multi-DRM
Every genuine copy of the video content is embedded with a unique code. In case if the content is leaked or pirated, the watermark detector can then be used on the pirated content copy for detecting the watermark. Based on the detection results, it can be known from where the content was first leaked/pirated.
Stages of Forensic Watermarking
While the working of a forensic watermarking solution can vary between providers, the basic functioning can be divided into five major steps-
-
-
Preparation
The first step is to prepare the video content for the watermark. The content goes through an encoder in this step, and the encoded content copy is then ready for embedding. In some of the watermarking solutions, content is simultaneously encoded and embedded.
-
Embedding
The embedder adds identifiers or information to the encoded content. The identifier can be the source of the video content or the intended recipient. This information is embedded into the content in the form of an invisible watermark.
-
Distribution
Once the content is embedded with a forensic watermark, it is then ready for distribution. Genuine copy of the video content can then be distributed among the intended recipients. It is possible that the content might get leaked or pirated at this stage.
-
Capture
If at all the content is leaked, the pirated content can be captured and monitored for collecting material evidence. OTT platforms, content creators, or pay-TV operators can do this on their own or work along with an anti-piracy solution or service.
-
Extraction
The identifiers embedded in the second step are then extracted from the pirated content copy. The watermark detector can then detect the exact source from where the content was leaked.
-
Based on the information, anti-piracy measures can then be taken to prevent such occurrences in the future. Legal proceedings can also be initiated against the source of the leak to effectively prevent piracy.
How Forensic Watermarking Works?
Now that you have a basic idea about the stages involved in forensic watermarking, it’ll be easier for you to understand how the technology works. There are three major aspects of forensic watermarking technology. They are as follows-
-
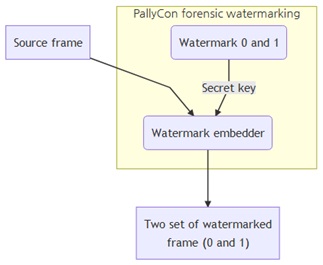
Watermark Embedder
As mentioned above, before the genuine video content is embedded, it first goes through the encoding process. During the encoding or preparation phase, a watermarked frame with values 0 and 1 is added to the original uncompressed content.
Working of the Watermark EmbedderThe embedder then inserts identifiers and generates two different copies of the encoded video content. The value of the identifier can only be encrypted with the help of a secret key, which is unique to every copy of encoded content.
Some solutions also come with multiple embedding options. Depending on the environment of the OTT platform or content creator, the embedding method can be selected from options like the embedder library, CLI embedder, or watermark packing service.
-
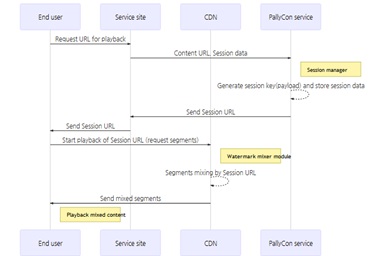
Watermark Mixer
The watermarking service will then combine both the versions of the video content (0 and 1) at the time of playback in real-time. Session information, like user ID, etc. is converted into binary format for composing the output which combines DASH and HLS content segments.
Working of the Watermark MixerDue to this, every single playback session is embedded with a unique and invisible watermark before it is streamed by a user.
-
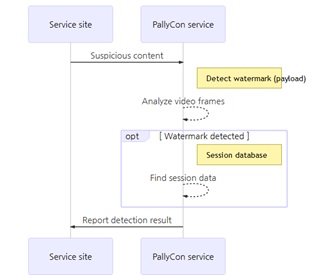
Watermark Detector
In case if the watermarked content is leaked at any point, the OTT platform, content creator, studio, or pay-TV operator can then detect the leaked content. The watermark detector then analyzes every frame of the pirated video content for identifying the original watermark.
Working of Watermark DetectorIt uses the same secret key that the embedder used at the time of inserting the watermark. If the detection process finds the watermark payload, the session database can then be used for finding the session information that matches the payload key value.
The detection result is then presented to the OTT platform or content creator to help them find the exact source from where the content was leaked.
Key Features of PallyCon’s Forensic Watermarking
PallyCon, a leading forensic watermarking solution, is used by global OTT platforms, production studios, content creators, and pay-TV operators for protecting their premium video content. Here are some of the top features of PallyCon’s forensic watermarking services–
-
First Global SaaS Service
PallyCon is the world’s first service provider to offer forensic watermarking and Multi DRM a single workflow in the cloud. The cloud service from the provider is built on AWS (Amazon Web Services), enabling the whole process of watermarking, starting from encoding to detection, Multi DRM to be completed in the cloud.
-
Robust and Imperceptible Watermarking
The robust and imperceptible watermarking from PallyCon is a powerful way for content platforms to protect their premium content against common attacks such as cropping, camcording, filtering, and reencoding. For enhanced protection, the watermarking service also complies with MovieLabs specifications.
-
Agile Watermark Detection Services
Apart from embedding content with robust watermarks, PallyCon also offers highly efficient watermark detection services. In case if the content is leaked at any point throughout its lifecycle, PallyCon can help the platform or content creator help find the source of the leak.
-
Pre-integrated with PallyCon Multi-DRM
Multi-DRM is a cost-efficient way for content platforms to protect their content while also increasing their reach across the globe. The forensic watermarking services from PallyCon come pre-integrated with its multi-DRM service for enhanced content protection.
PallyCon Forensic Watermarking Supports Specifications
Here is a list of specifications supported by PallyCon’s forensic watermarking service-
| Item | Specification |
|---|---|
| Content-Type | Video content |
| Format and codec | MP4 (CBR) VOD video, H.264/H.265 codec (Live video to be supported soon) |
| Supported Resolution | Up to 4K/UHD resolution |
| Dynamic Range | Standard Dynamic Range (SDR) supported (HDR to be supported soon) |
| Streaming Protocol | MPEG-DASH, HLS (HTTP Live Streaming) |
| CDN Integration | AWS CloudFront CDN |
| Watermark Data Size | Up to 255-byte string using mapping table |
| DRM Integration | Multi-DRM (Widevine, PlayReady, FairPlay) |
Forensic Watermarking in Mobile Devices
More and more people now use their mobile phones for streaming and downloading video content. While content creators and OTT platforms are aiming to target more mobile consumers, illegal distribution of the premium downloaded content from mobile phones is a growing threat. Until now, the only way to limit illegal distribution was DRM.
Digital Rights Management (DRM) enables content creators and distributors to limit the number of devices on which their content could be played. For instance, music that you purchase from the iTunes Store can only be played on authorized devices such as Apple iPod and some authorized computers. This is possible with the help of Apple’s FairPlay DRM which is used by the iTunes Store.
But DRM makes content streaming highly restrictive as content from certain sources could only be viewed on certain devices. Forensic watermarking helps reduce the limitations imposed by DRM on mobile devices. The technology can be used to add imperceptible information or code to every unique copy of genuine video content that is streamed or downloaded to mobile devices.
If the downloaded copy is then screen-recorded or illegally distributed in vast numbers, the content creators are then able to find the source from where the leak took place. So, apart from premium video content on computers and laptops, forensic watermarking is an innovative and effective way to prevent piracy through mobile devices and tablets too.
Irremovable and Imperceptible Marking
No video processing technique, like scaling, resizing, or encoding, could be used to manipulate the unique watermarking embedded into the video by PallyCon forensic watermarking service. Each genuine copy of the content is embedded with a unique watermark payload that is associated with a serial number that can be used for defining the content source.
But none of the personally identifiable data is ever attached to the content. This ensures that the watermark functions as a powerful deterrent to the cybercriminals without impacting the user experience in any way. Moreover, as the watermark is invisible to the human eye, there is again no risk of negatively affecting the viewing experience of the users.
Session-Based Watermarking
With the help of standard watermarking, OTT platforms and content creators could find out the exact source from where the content was leaked. But the platforms still need a way to recognize the user accounts so that the watermark detection result can be used for pointing out the individual responsible for the leak.
Session-based watermarking offered by PallyCon can help in this aspect too. As discussed above, the technique uses two different versions of the same content with different identifiers. Session-based manifests are then generated on the origin server along with segmented lists of all the various chunks of combinations.
With this method, every chunk is used either from track 0 or track 1. This helps in binary representation, which can then be used for creating unique manifests for every individual session. Moreover, it eliminates the need for creating or storing as many content versions as there are paid users.
With session-based watermarking, only two copies are created, which are then cached on any CDN. This also eliminates the need for any client-side 3rd party library integrations as all the required information is already stored inside the server-side manifests. To help reduce storage space requirements, watermarks can also be embedded on selected chunk locations.
PallyCon Forensic Watermarking for Protecting Premium Video Content
Piracy has always been a threat to producers, studios, and content creators. But in this age where the popularity of video streaming is at an all-time high and is only expected to grow further, inadequate anti-piracy measures could lead to significant revenue losses.
By combining PallyCon’s multi-DRM service and forensic watermarking service, OTT platforms, creators, and studios could effectively limit video piracy throughout the lifecycle of their content. Over time, this could help them reach newer paid users and improve their revenue.

PallyCon provides cloud-based SaaS multi-DRM solution and Forensic Watermarking service. Cloud services built on AWS enables you to use services in the cloud. Get started contents protection quickly and easily with PallyCon.