
How Google’s Widevine DRM Prevents HD, Ultra-HD Video Leakage to Piracy Market
The world watches videos on over-the-top platforms (OTT), like Netflix and Amazon Prime, now, and has almost fully moved over the earlier days of owning or possessing video files in their devices. Such ease of viewing the same videos across devices of users creates challenges for content producers and owners, piracy being the biggest of them alongside restricting concurrent streams on one subscription plan. The other great challenge is to deliver HD content to the user’s devices while ensuring that the device offers enough security at the level of hardware and software to prevent leakages.
The answer to these challenges is a digital rights management (DRM) solution. One of the most popular DRM solution to protect HD content is Google’s Widevine, which can be implemented on Chrome and Firefox web browsers, Android OS on mobile devices and smart TVs among others. Most popular OTT players and video-streaming services use Widevine to protect their content.
Widevine protects video streams at three levels involving the device hardware and code. At the heart of this DRM protection is CENC or common encryption protection scheme, which specifies encryption standards and key mapping methods that a DRM content decryption module (CDM) uses to decrypt video files at the client device. Widevine uses CENC protocols to bind video files to licensing keys that it issues to content packagers, such as the one offered by PallyCon, and allows the client device to play videos at adaptive bitrates. Adaptive streaming is a crucial requirement of content producers, as they do not want to allow access to HD content on unsecure devices for the fear of revenue leakage due to piracy.
Widevine defines security levels as L1, L2, and L3, where the L1 level is considered most secure for playing premium HD videos from OTT majors. Widevine depends on the trusted execution environment (TEE) of the device’s processor to implement L1 security for premium video delivery. Since the TEE allows code and data protection inside a safe zone in the processor, where execution takes place independent of the operating system processes and the code can use full potential of the processor and memory, it is considered a more secure process and less vulnerable to manipulation by hackers. Moreover, the applications inside the TEE are hardware dependent, where encryption keys are embedded in the processor chip, thus making tampering almost impossible. Widevine uses the TEE to create a separate zone for execution of its code for the L1 level security. At this level, both cryptography and video processing takes place inside the TEE.
Google Widevine’s Security Level:-
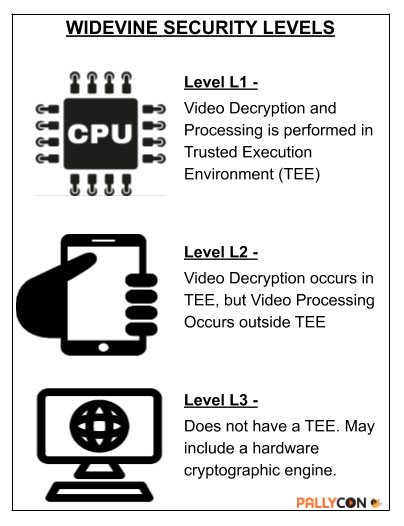 Where hardware or licensing limitations do not permit original equipment manufacturers (OEMs) to implement the L1 level of security, Widevine offers L2 and L3 levels. The L2 level, considered a step below L1, allows cryptography to reside at the TEE but processes videos outside. On the other hand, the L3 level lets both cryptography and video processing take place outside the TEE or is implemented where the TEE is not an option. Most desktop CDM operate at the L3 level, while Android devices generally have the L1 level of security. The L1 layers operate within Arm TrustZone technology, which most chipset manufacturers use to create the TEE. The important thing to note here is that Widevine, being a trusted software placed under the trusted zone of the CPU, decrypts the encrypted video content within this space of the CPU. The Android OS, then, plays back this content by initiating a secure session using a video driver.
Where hardware or licensing limitations do not permit original equipment manufacturers (OEMs) to implement the L1 level of security, Widevine offers L2 and L3 levels. The L2 level, considered a step below L1, allows cryptography to reside at the TEE but processes videos outside. On the other hand, the L3 level lets both cryptography and video processing take place outside the TEE or is implemented where the TEE is not an option. Most desktop CDM operate at the L3 level, while Android devices generally have the L1 level of security. The L1 layers operate within Arm TrustZone technology, which most chipset manufacturers use to create the TEE. The important thing to note here is that Widevine, being a trusted software placed under the trusted zone of the CPU, decrypts the encrypted video content within this space of the CPU. The Android OS, then, plays back this content by initiating a secure session using a video driver.
From the user’s perspective, the L3 level is not desirable since content producers expect DRMs to deliver only sub-HD resolutions in browsers or apps, which impact user experience, especially in the case of premium content. The user, therefore, can get the optimal delivery of a video asset in the form of HD and ultra-HD content only where the device is L1 compliant.
Google purchased Widevine Technologies in 2010. This was also the time when OTT platforms were gaining popularity on the back of the internet becoming cheaper and the arrival of affordable smartphones and subsequent popularity of Android OS. The earlier version of Widevine that catered to this period up to Android 5.1 and Samsung and LG smart TVs was called Widevine Classic. It worked only with the .wmv format of video content. A more developed version, which caters to modern devices and higher versions of Android and web browsers, is called Widevine Modular. It supports MPEG-DASH, HLS, and CMAF formats and adaptive bitrates.
The browser support from Widevine falls under the L3 level of security, but Widevine keeps innovating to make it more secure. Its latest effort to stem leakages from web browsers is verified media path (VMP) technology. VMP allows Widevine to verify the authenticity of the browser framework and check if a browser framework is playing the legal content or not. Most browsers that support Widevine CDM include support for VMP as well.

PallyCon provides cloud-based SaaS multi-DRM solution and Forensic Watermarking service. Cloud services built on AWS enables you to use services in the cloud. Get started contents protection quickly and easily with PallyCon.

