How does Watermark Embedder use Cloud Servers to Mix A-B Segments of Protected Videos?
The rising demand for video-on-demand (VoD) and over-the-top (OTT) content has furthered the need for additional protection to online video content against leaks and illegal usage. With a shift in video piracy away from peer-to-peer networks and illicit downloads to illegal real time streaming, the problem of content piracy has dramatically increased. Digital watermarking techniques have, thus, gained acceptance as an additional layer of protection for the content which is otherwise protected through digital rights management (DRM) technology.
Video watermarking technology is essentially an information-hiding technology that indirectly embeds identification information in the digital media without compromising the value of the original carrier. In case of content infringement, watermarks can be extracted to identify the content owner, transmit the hidden information, and identify the source of infringement. The three most essential characteristics in a digital watermark are imperceptibility, security, and robustness.
Common video watermarking techniques
The most common methods of video watermarking currently in use are bitstream modification, client-side watermarking, and A/B variant watermarking. Bitstream modification involves modifying selected areas of a picture or video frame in a non-impactful way (by maintaining the video quality) so that the user and session can be identified in a leaked fram. Client-side watermarking is the most commonly used method and is preferred because of its deployability across multiple platforms, rapid watermark extraction, and low cost complications. In this technique, a graphical overlay is composited onto the video stream in the client device.
A/B variant watermarking
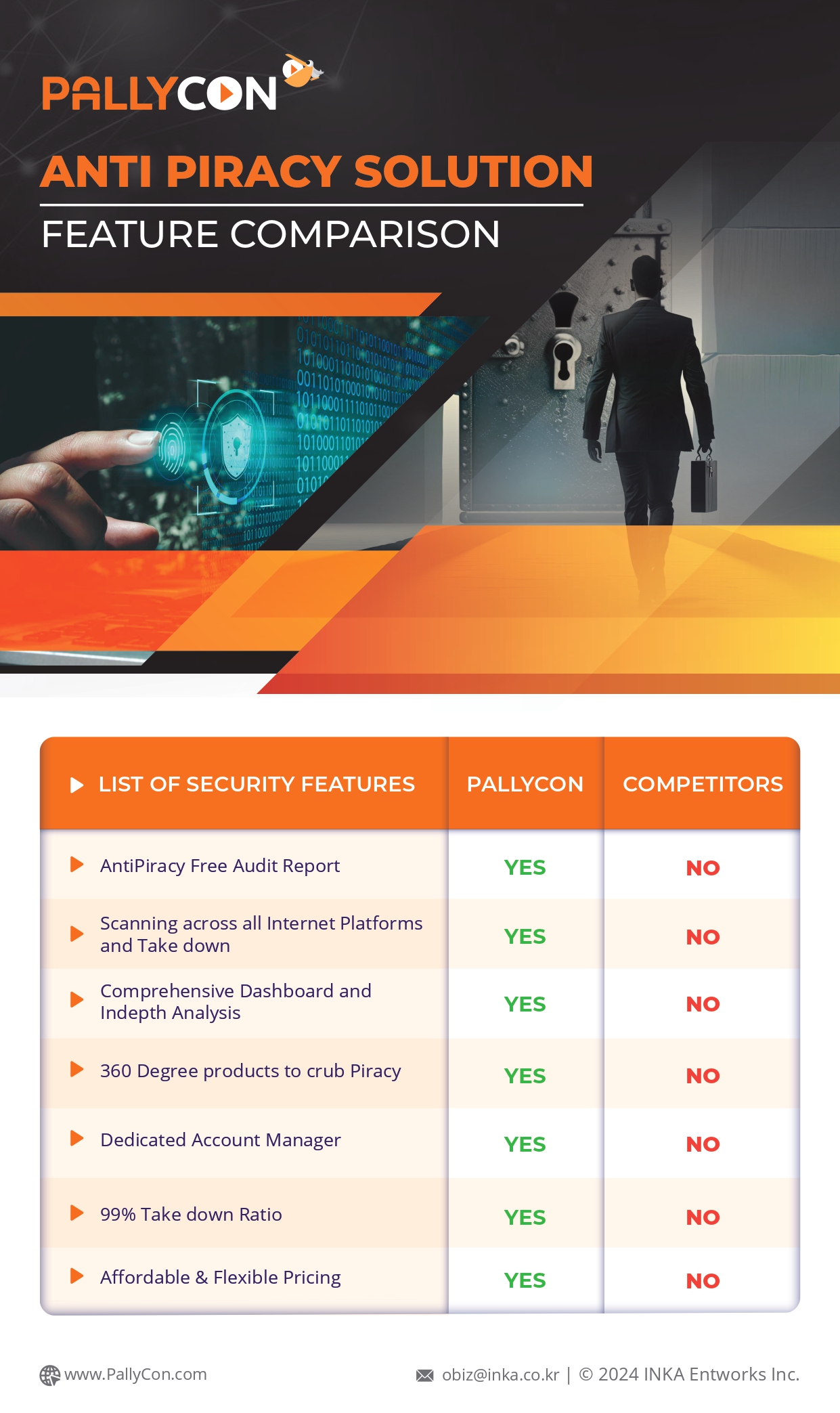
A/B variant watermarking, on the other hand, is primarily used in the OTT and VoD space. Here, two copies of a video stream (marked A and B) are created which are totally similar except for the watermark. In A/B watermarking, pixels are modified in the transcoder, and the content undergoes some pre-processing to identify the modifiable pixels and modify them without compromising the quality of the video. This pre-processing data is then fed into the transcoder where the pixels are modified. The assets are segmented into chunks so that the playouts have a unique pattern of As and Bs. Different values (A/B or 0/1) are inserted in the original video frames and the output is given as two sets (A/B) on the encoded video.
In this way, two content copies are used to create a unique manifest for each subscriber session. The session information, such as the user ID, is converted to binary format and the outstream is composed by combining segments from the DASH and HLS content. Finally, the packager combines the A/B video segments from each of the two copies to create a unique manifest. The segments are delivered in a unique order according to the watermark payload for the session information. The watermark on this unique manifest can then be used to identify the original customer of an illegally shared piece of content. The process of interleaving, either client-side or via content delivery network (CDN) edge processing, provides the unique identifier.
How edge servers handle A/B segments
The selection of A/B segments is performed just-in-time for each client segment request. Here, the serialization step of the two-step watermarking system is performed in edge servers. All recipients receive the same playlists, while the video delivery system still needs to deliver a unique sequence of A and B segments to every individual. To achieve this, edge servers select either A or B version of the segment to be returned when they receive a segment request. After the segment version has been selected, the edge server can query the cache to the origin server which then delivers it to the recipient. The edge server is capable of deciding which segment to deliver.
This solution has the same CDN caching properties as the playlist embedding for the content while also giving the additional advantage of caching the playlist. This method may be required in cases where byte-range indexed playlists are used, or the playlist is templated (such as with Smooth Streaming and DASH VoD profiles), and segments cannot be addressed individually.
The serialization effort during playlist delivery is eliminated and the same playlist can be used for all streams. The logic used by the edge server to decide for each requested segment includes identification of the information to be embedded, a decision for segment selection, and the delivery of the corresponding segment. The fact that all recipients receive the same playlist provides an extra layer of security against comparison and manipulation of playlists before the content is downloaded. The segment list of the DASH manifest (.mpd) or HLS playlist passed as a session URL applies the same path and filename to all users, regardless of session information. This makes A/B watermarking safe from segment naming attacks, where segment lists of multiple sessions are mixed for the same content. It is recommended to make use of https-based segment URIs or other strategies to avoid local ISPs from further caching the seemingly “common” content segments after they leave the CDN edge, thus destroying the A/B serialization pattern.
Some edge servers can perform late repackaging operations on the segment content itself. This allows segments to be selected on the edge allowing choice between A/B, while also preceding assembly of these segments even after they have been requested. A single video transport protocol is, thus, used between the origin server and edge servers to optimize caching capabilities and perform repackaging operations (container and scrambling) at the edge to deliver segments in the desired format.
A/B forensic watermarking can, thus, be used to protect OTT content from piracy and illegal usage. However, the only drawback of this technique is that the watermark extraction is slow as the identifying sequence can be long, especially for clients with a large subscriber base. It also requires increased delivery infrastructure because of the dual-stream approach.
The PallyCon advantage
PallyCon handles this complicated process of edge server mixing of segments for video watermarking in a single workflow. Content owners can use PallyCon to manage their DRM licenses from multiple vendors, like Widevine, FairPlay, and PlayReady and integrate forensic watermarks to identify individual sessions at the client device with ease and one subscription plan. It helps content owners to not just embed watermarks in their premium assets but also extract them with ease when they detect content leakage.
Get Forensic Watermarking White Paper Now!

PallyCon provides cloud-based SaaS multi-DRM solution and Forensic Watermarking service. Cloud services built on AWS enables you to use services in the cloud. Get started contents protection quickly and easily with PallyCon.