Understanding Software DRM Vulnerabilities and How PallyCon DRM License Cipher Solution Enhances Security
Digital Rights Management (DRM) is a crucial technology for protecting digital content from unauthorized access and distribution. However, not all DRM implementations offer the same level of security. Software-based DRM solutions, such as Widevine L3, are particularly vulnerable to various hacking techniques. This blog article explores the vulnerabilities of software DRM and introduces the PallyCon DRM License Cipher solution, which enhances DRM security by leveraging advanced cryptographic techniques.
Widevine L3 CDM Vulnerability
Widevine is a DRM technology developed by Google, widely used in streaming services. It operates at three security levels: L1, L2, and L3. Widevine L1 provides the highest level of security by leveraging hardware-based Trusted Execution Environments (TEE). In contrast, Widevine L3, which relies solely on software, is more susceptible to attacks. The main vulnerability of Widevine L3 lies in its software-based nature, making it easier for attackers to reverse-engineer the code and extract decryption keys.
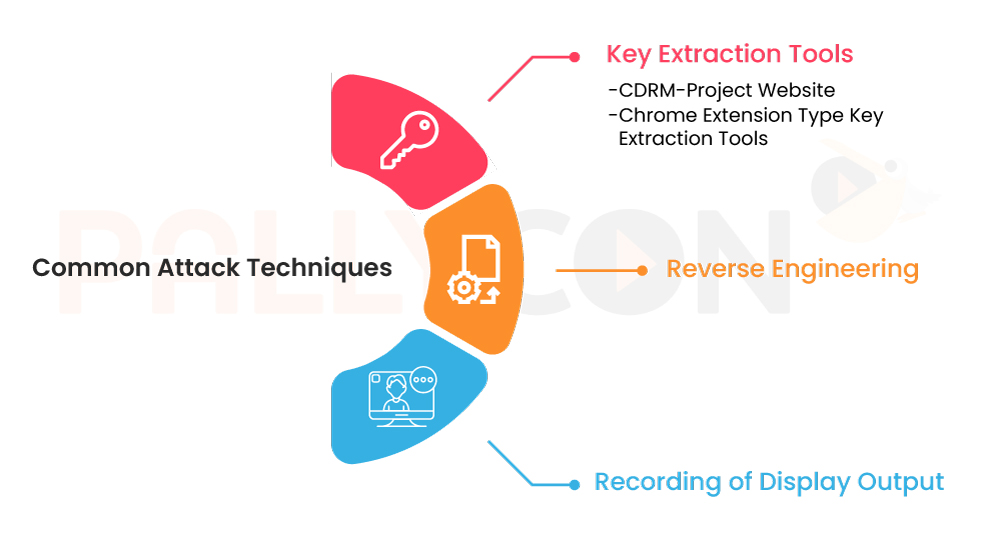
Common Attack Techniques
-
- Key Extraction Tools:
- CDRM-Project Website: This platform provides tools and methods to bypass DRM protections, particularly targeting software-based DRM like Widevine L3.
- Chrome Extension Type Key Extraction Tools: These tools operate as browser extensions, intercepting the communication between the DRM client and the license server to extract decryption keys.
- Reverse Engineering:
- By reverse-engineering the DRM client software, attackers can uncover vulnerabilities and exploit them to extract decryption keys or bypass DRM protections entirely.
- Recording of Display Output
- When there is not enough level of output protection, attackers can capture the playback output after authorized DRM decryption. The type of attack does not require the DRM key extraction.
- Key Extraction Tools:
Impact on Content Security
The vulnerabilities in software DRM solutions like Widevine L3 compromise the security of DRM-protected content, leading to unauthorized access and distribution. This not only affects the revenue of content providers but also undermines the trust in DRM technologies.
Introducing PallyCon DRM License Cipher Solution
To address these vulnerabilities, PallyCon has developed the DRM License Cipher solution. This advanced security measure enhances DRM protection by ensuring that licenses are issued only to authenticated and authorized client applications.
Core Features of PallyCon DRM License Cipher
- Whitebox Cryptography (WBC) Technology:
- Definition: Whitebox Cryptography is designed to protect cryptographic keys even when the attacker has full access to the software implementation, including the ability to observe, modify, and debug the execution.
- Application in PallyCon: PallyCon uses WBC to prevent the exposure of its own encryption key data, ensuring that the keys cannot be easily extracted by malicious actors.
- WebAssembly (Wasm) Implementation for Web Applications:
- Purpose: WebAssembly is a binary instruction format that allows code to run at near-native speed in web browsers. It is designed to be portable, efficient, and secure.
- Benefits:
- Avoids Additional Installations: The WBC library built in WebAssembly eliminates the need for users to install additional components like Chrome extensions.
- Enhanced Security: WebAssembly modules run in a secure sandboxed environment, reducing the risk of exploitation.
How PallyCon DRM License Cipher Works
- License Request Encryption:
- When a client application (either on Android or web) requests a DRM license, the request data is encrypted using the WBC library.
- This encryption ensures the authentication of the client application, confirming that the request is coming from a legitimate source.
- Authentication of Client Application:
- The PallyCon License Server processes the encrypted license request data to verify the authenticity of the client application.
- Only authenticated and authorized applications receive the DRM license, preventing unauthorized clients and key extraction tools from obtaining the license.
- DRM License Issuance:
- Upon successful authentication, the DRM license is issued to the legitimate client application.
- The issued DRM license itself is not encrypted by the License Cipher solution, as the primary goal is to ensure that licenses are granted only to authorized clients.
- Decryption Key Usage:
- Once the DRM license is issued, the application can use the keys provided in the license to decrypt and play the DRM-protected content.
More on License Cipher SDK Guide here
Key Benefits of PallyCon DRM License Cipher
- Enhanced Security:
- By ensuring that DRM licenses are issued only to authenticated and authorized client applications, the PallyCon DRM License Cipher solution significantly reduces the risk of unauthorized access and key extraction.
- Cross-Platform Support:
- The solution supports both Android and web platforms, making it versatile and easy to integrate across different types of applications.
- User-Friendly Implementation:
- The WebAssembly-based approach for web applications provides robust security without requiring users to install additional software, ensuring a smooth and user-friendly experience.
Conclusion
Software-based DRM solutions, such as Widevine L3, are inherently vulnerable to various attack techniques, compromising the security of digital content. The PallyCon DRM License Cipher solution addresses these vulnerabilities by leveraging Whitebox Cryptography to authenticate client applications and ensure that DRM licenses are issued only to authorized clients. By implementing this advanced security measure, content providers can significantly enhance the protection of their digital assets, safeguarding them against unauthorized access and distribution.
By understanding the vulnerabilities of software DRM and implementing solutions like PallyCon DRM License Cipher, content providers can maintain the integrity and confidentiality of their media assets, ensuring a secure and reliable content ecosystem.

Govindraj is a Global Business Head for PallyCon at INKA Entworks. He keenly follows the innovation and development in content security, application security, and software development, he loves to educate everyone about the what, why, and how of major incidents in the content protection world. His views on industry trends and best practices have been featured in articles, white papers, and had been a keynote guest at multiple security events.